As attacks on sites become more common, solutions to defeat those attacks are created. Security can be daunting for non-technical site owners to understand. Security is complex and technical. Fortunately for us, some of the newer solutions provide explanations and videos.

How much you need to know about security depends on your job and why you are interested. If you only want to secure your personal blog or site, your hosting company will provide at least some protection. Unfortunately, it may not be enough protection.
Hackers trying to access WordPress blogs are very common as are hackers getting into eCommerce sites. Prevention is always far superior to having to repair the damage hackers can do. Fortunately, there are solutions that make it easier to block hackers and prevent them from accessing our sites.
This video about FireBlade security provides a visual idea what security solutions do:
Video Highlights:
- Fireblade dashboard shows availability, threat analysis and security status
- Firewall policies to block threats
- Firewall static rules
- Statistical highlights including server errors
- Whitelist or blacklist IPs
- DDoS protection (anti-DDoS)
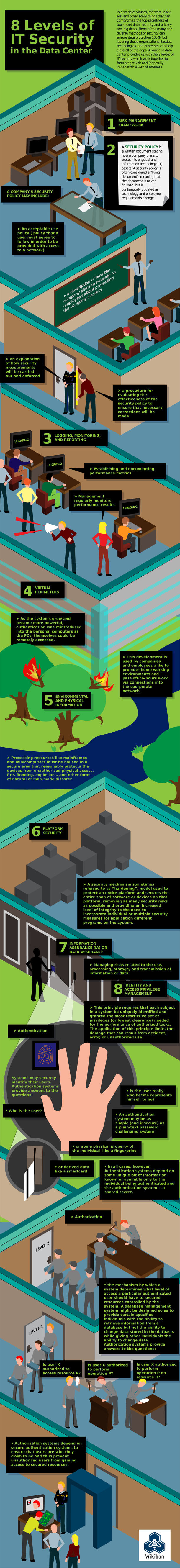
Security solutions like FireBlade provide part of what is required. Your hosting company should provide additional security measures. The infographic below contains a more complete list of what is required:
1) Risk Management Framework
Your hosting company should have a risk management framework that contains:
2) Security Policy
A continuously updated written document detailing how physical and IT assets are protected.
3) Logging, monitoring and reporting
Automated solutions such as the one explained in the video above are employed to handle this aspect.
4) Virtual Perimeters
Virtual perimeters are used to enhance network protection and protection against DDoS (Distributed Denial of Service) attacks.
5) Environmental and Physical Information
Protection of the physical computer room and network from attacks and weather related dangers.
6) Platform Security
According to the DRM dictionary: “A security paradigm according to which the platform (e.g. Operating System and possibly hardware) protects software programs from attack, so that the programs do not need to protect themselves.”
7) Information Assurance / Data Assurance
According to Iowa State University: “Information assurance (IA, InfAs) is the practice of managing information-related risks. More specifically, IA practitioners seek to protect and defend information and information systems by ensuring confidentiality, integrity, authentication, availability, and non-repudiation.”
8) Identity and Access Privilege Management
Controlling physical access and only granting access to those who need it. Methods of access restriction are elaborated on in the infographic below: